Attack paths allow adversaries to reliably take control of nearly every Active Directory in the world.

Microsoft Active Directory (AD) and Azure Active Directory are the dominant directory service products that provide critical services to organizations, including identity and access management, endpoint management, business application management, and much more. AD was introduced with Windows 2000 Server edition and has been a favorite target for attackers ever since.
You might think that two decades is long enough to identify and fix the fundamental security issues associated with such a foundational product — but this isn't the case. Two of my colleagues recently published research into one specific aspect of AD security, AD Certificate Services, and found that nearly every AD environment they examined had misconfigurations that could create critical attack paths.
Why then, 20 years later, are adversaries still targeting AD? Let's explore five answers to that question and discuss how AD security can be improved.
1. If At First You Don't Succeed…
When it comes to AD, attackers get unlimited retries — with no real consequences for failure. Even if they're identified and kicked off the network, the experience allows them to learn more about the AD environment and apply that knowledge to future attacks. Mapping these attack paths (chains of users and machines with abusable access connecting them) makes it more likely that future attacks will succeed. For example, here is a real set of attack paths leading from domain users to domain admins in an actual environment:
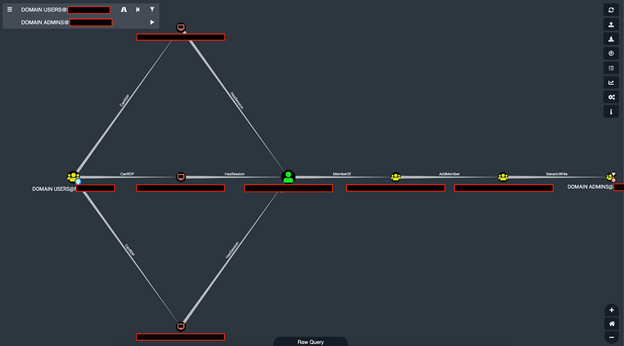
Several attack paths leading from the domain users group to the domain admins group viewed in BloodHound. These attack paths include lateral-movement and AD object-takeover steps.
2. It Holds the Keys to the Kingdom
Targeting AD will almost always help attackers reach their objective, whether that's accessing sensitive data, deploying ransomware, or conducting nation-state espionage. When an endpoint is joined to AD, several mechanisms allow AD administrators to take control of that endpoint. These are used legitimately for things like installing antivirus and configuring local security policies but can also be abused by attackers to take control of any endpoint they want.
Even when a system is not joined to AD, it may still be used to validate the identity of a user with access to that system. Think of technologies like Remote Authentication Dial-In User Service (RADIUS) or single sign-on (SSO) — AD validates the user for the system, and then the system grants the user access. For the adversary, gaining control of the identity authority (AD) means they can give themselves the access needed to take over any system, user, business process, data, etc. AD is the metaphorical "key to the kingdom" that lets adversaries unlock any door they need.
3. AD Helps Attackers Stay Hidden
Once they have control of AD, attackers have strong options for maintaining persistence in the network. Most defenders already struggle with detecting commodity-level persistence mechanisms like malicious scheduled tasks, and the vast majority are not equipped or staffed to handle kernel-level persistence mechanisms. Control of AD means control of the operating system on every domain-joined machine, including domain controllers. With control of the operating system, the adversary can cause pieces of the operating system queried by defenders to report everything is fine, hiding themselves from defenders or threat hunters.
4. Good and Bad Admin Behavior Looks the Same
AD is attractive to attackers because it gives them plenty of ways to hide from defenders. Adversaries often use built-in, legitimate administrative tools and abuse existing privileges and permissions in AD. This makes it very difficult for defenders to tell the difference between "good" and "bad" admin behavior. Add the many defensive evasion techniques like code obfuscation or disabling endpoint security protections that attackers have at their disposal, and avoiding detection becomes much easier.
5. Shared Weaknesses
AD is the most common directory service in the world — the vast majority of the Fortune 500 use AD as do countless banks, healthcare systems, and government agencies. That means attackers can use the same techniques to attack AD at multiple targets since each installation will share the same weaknesses.
First among these weaknesses is that AD makes it very difficult to answer the question "How many users have administrator rights on this computer?" AD's interface only shows which principals have a direct "admin rights" relationship to a computer or object. A principal can be a single user or a group of users, and there's no easy way to see the individual members of those groups. These nested security groups make it almost impossible for teams to get an accurate picture of who has abusable access to crucial systems — and attackers can exploit that confusion. In one extreme case, I found an environment where AD showed 31 security principals in its local admin group, but when you counted all the individual users in nested groups, 733,415 users had admin rights!
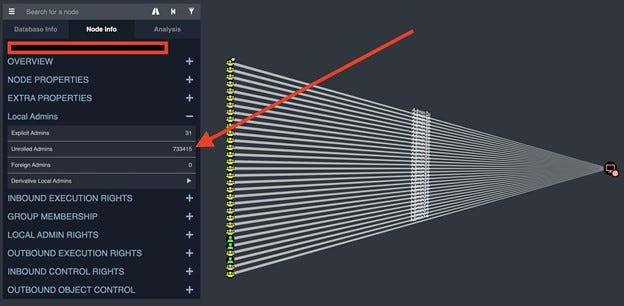
A real-life AD environment, viewed in BloodHound, with an extremely high discrepancy between explicit admins and unrolled admins.
This information is not meant to scare AD admins. On the contrary, I want to give a realistic view of AD security risks. Since AD makes it difficult to see who has admin access to crucial systems, it can be easy to underestimate the risk attack paths pose.
Better security starts with getting better visibility into AD, possible attack paths, and misconfigurations. Organizations could have hundreds or thousands of attack paths, so they need a way of identifying high-risk ones so that they know where to focus. Open source tools that can help with this include BloodHound (a free tool I co-created that maps attack paths in AD and Azure) and PingCastle (an AD enumeration and risk-assessment tool). IT also needs to have a plan for how to deal with misconfigurations, changes to the network, and limiting the effects of a compromise. Some good resources for securing AD include Microsoft's Securing Privileged Access documentation and ADSecurity.org.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




